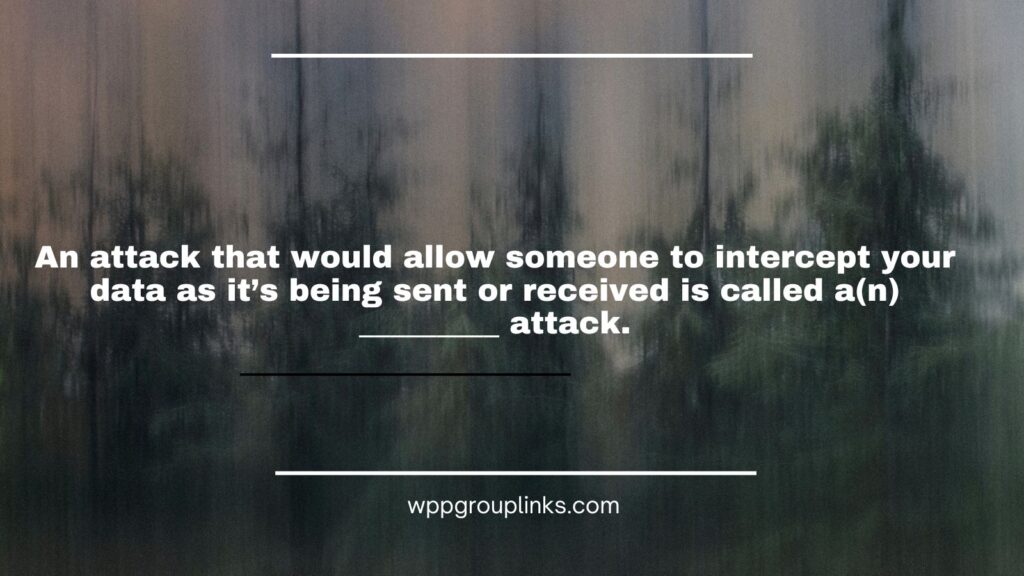
Q: An attack that would allow someone to intercept your data as it’s being sent or received is called a(n) _________ attack.
or
Q: The term “a(n) _________ attack” refers to a cyberattack that might enable someone to intercept your data in transit.
- SYN flood
- Denial of Service
- Man-in-the-middle
- Injection
Explanation: An assault that is known as a “Man-in-the-Middle” (MitM) attack gives an individual the ability to intercept your data while it is being sent or received. An assault known as a “Man in the Middle” occurs when an adversary stealthily intercepts and maybe modifies the communication that is taking place between two parties without the awareness of those parties. Because of this, the integrity and confidentiality of the data that is being communicated may be jeopardized. Man-in-the-middle attacks can take place in a variety of settings, including during online purchases, communication via Wi-Fi, or email exchanges. A reduction in the likelihood of Man-in-the-Middle attacks may be achieved by the use of secure communication routes, encryption, and the verification of the validity of communication endpoints.